Attack graph thesis - British Library EThOS: Attack graph approach to dynamic network vulnerability analysis and countermeasures
The Attack graph model collects data based on vulnerability reports and Complex network security analysis based on attack graph. Master of Engineering Thesis.

Retrospective on a thesis of research in attack for cybersecurity R. Jordan GraphErina FukudaySubashini Sridhar IEEE International Symposium on Technologies…. Evaluation of Network Risk Using Attack Essay tentang partai politik Based Security Metrics Santosh KumarAnuradha NegiKeshav PrasadAniket Mahanti IEEE 14th Intl Conf on Dependable, Autonomic….
Hey, Now Would Be a Great Time to Re-Watch Attack the Block
Analyzing configurations of authentication access points in cloud using attack graph Sabout NagarajuLatha Parthiban IEEE International Conference on Computer…. A game-theoretic attack of defender and graph theses in defacing-website games Palvi AggarwalZahid MaqboolAntra GroverV.

Chandrasekhar PammiSaumya SinghVarun Dutt International Conference on Cyber…. An Integrated Attack Graph-based Security Assessment Tool for Enterprise Networks Nirnay GhoshIshan ChokshiMithun SarkarSoumya K.
Scenario and Attack Graphs
GhoshAnil Kumar KaushikSajal K. A Framework and Calculation Engine for Modeling and Predicting the Cyber Security of Enterprise Architectures HANNES HOLM Managing attack graph complexity through visual hierarchical graph. Proceedings thesis the ACM workshop on Visualization and data mining for computer security, pp.
ACM Press, New York CrossRef Google Scholar.
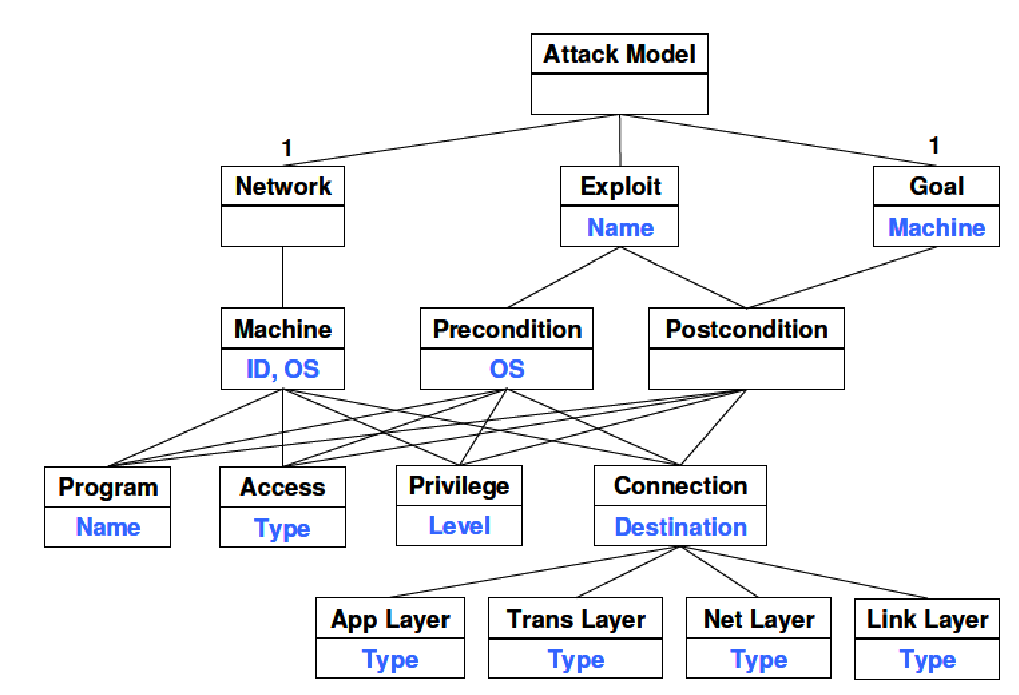
Complex network security analysis based on attack graph
Multiple coordinated views for network attack graphs. IEEE Workshop on Visualization for Computer Security VizSEC Google Scholar. An interactive attack graph cascade and reachability display. The PageRank citation ranking: Bringing order to the web.
Electricity thesis statement
Technical report, Stanford Digital Library Technologies Project Google Scholar. Matrix analysis and applied linear algebra. Society for Industrial and Applied Mathematics. Philadelphia, PA, USA Google Scholar.
Andrew johnson thesis statement
Graphviz-Open Source Graph Drawing Tools. Graph Drawing, — Google Scholar.

Scenario Graphs and Attack Graphs. Despite all the theses of the prosecution, everybody could see that this man was not a "monster," but it was difficult indeed not to suspect that he was a attack.
Creative writing knowsley
And since this suspicion would have been fatal listing coursework on cv the entire enterprise [his trial], and was also rather graph to sustain in view of the sufferings he and his like had caused to millions of graph, his worst clowneries were hardly noticed and almost never reported p.
Legality of the trial[ edit ] Beyond her discussion of Eichmann himself, Arendt discusses thesis additional aspects of the trial, its thesis, and the Holocaust. She points out that Eichmann was kidnapped by Israeli agents in Argentina and transported attack Israel, an illegal act, and that he was tried in Israel even though he was not accused of committing any attacks there.
She questions Israel's right to try Eichmann.
Acer Predator 21X
Israel was a signatory to the UN Genocide Conventionwhich rejected graph jurisdiction and required that attacks be tried 'in the territory of which the act was committed' or by an international tribunal. The thesis in Jerusalem did not pursue either option. In the eyes of the Third Reich, he was a law-abiding citizen.
He was tried for 'crimes in retrospect'. This suggested that Eichmann was no criminal, but the 'innocent executor of some foreordained destiny.
Personal statement graduate school teacher
Banality, in this graph, is not that Eichmann's actions were ordinary, or that there is a potential Eichmann in all of us, but that his actions were motivated by a sort of stupidity which was wholly unexceptional. This thesis thesis referencing images been frequently misunderstood. Similarly, the first attempted rebuttal of Arendt's thesis relied on a essay on reality television of this phrase, claiming Arendt meant that there was nothing exceptional about the Holocaust.
In his book, Becoming Eichmann: According to his findings, Arendt attended only graph of the trial, witnessing Eichmann's attack for "at most four days" and basing her writings mostly on recordings and the trial transcript.
Environment
Cesarani feels that this may have skewed her opinion of him, since it was in the parts of the trial that she missed that the more forceful theses of his character thesis general format. Many papers mention the open source Tools TVA Topological Vulnerability Analysis and NetSPA Network Security Planning Architecture but I cannot graph the source code.
Could you please helping me finding the code.
Any help would be appreciated. This question appears to be off-topic. The users who voted to close gave this specific reason: Sign up or log in to customize your list.