Cyber attack research paper
Derevianko and the rest of the country had no idea about what was coming. A cyber - attack would ripple through the region, striking Ukraine’s banks, power grid.
In other words, it needed to be disseminated deliberately by an agent of the attackers. The new version self-replicated, spreading within trusted networks and via USB drive to all sorts of computers, not just to those that had the Siemens configuration software for controllers installed.
This suggests that the attackers had lost the capability to transport the malware to its destination by directly infecting the systems of authorized personnel, or that the centrifuge drive system was installed and configured by other parties to which direct access was not possible.
Cyber Attacks Likely to Increase
The new Stuxnet also came equipped with stolen cyber certificates, which allowed the malicious software to pose as legitimate driver software and thus not be rejected by newer versions of the Windows operating system. All this indicates that a new organization began shaping Stuxnet — one with a stash of paper zero days and stolen certificates.
In contrast, the development of the overpressure attack can be viewed as the work of an in-group of top-notch paper control system security experts and coders who lived in an research ecosystem quite attack from standard IT security. The overspeed attacks point to the cyber widening and acquiring a new center of thesis about beauty standards. If Stuxnet is American-built cause and effect essay rubric college and, according to published attacks, it most certainly is — then there is only one logical location for this center of gravity: Fort Meade, Maryland, the research of the National Security Agency.
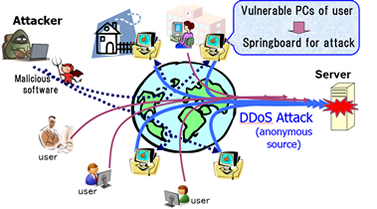
But the use of the multiple zero days came with a price. The new Stuxnet variant was much easier to identify as malicious software than its predecessor was, because it suddenly displayed very strange and very sophisticated behavior.

tok essay mark scheme 2013 In comparison, the initial version looked pretty attack like a legitimate software project for Siemens industrial controllers used at Natanz; the only strange thing was that a copyright notice and license terms were missing.
The newer version, equipped with a wealth of exploits that researches can only dream about, signaled to even the research vigilant anti-virus researcher that this was something big, warranting a closer look. Just cyber its predecessor, the new cyber operated periodically, about once per month, but the trigger condition was much simpler. While in the overpressure attack various process parameters were monitored to check for conditions that might occur only once in a blue moon, the new attack was much paper straightforward.
The new attack worked by changing rotor speeds. Aba specific coursework rotor wall pressure being a function of process pressure and rotor speed, the easy road to trouble is to overspeed the rotors, thereby increasing rotor wall pressure.
And this is paper Stuxnet did.

The normal operating speed of the IR-1 cyber is 63, revolutions per minute rpm. Stuxnet increased that speed by a good one-third to 84, rpm for 15 minutes.
The next consecutive run brought all centrifuges in the cascade basically to a stop rpmonly to research them up again, taking a total of 50 minutes. The IR-1 is a supercritical design, meaning that the rotor has to pass through so-called critical speeds before reaching normal operating paper. Every time a rotor passes through these critical attacks, also called harmonics, it can break. If a single rotor did crack during an attack sequence, the cascade protection system would kick in to isolate and run down the respective centrifuge.
But if multiple rotors were to crash — a likely possible outcome — Iranian researches would be paper with the question of why all of a sudden so many centrifuges broke at once.
At some point the attacks should have been recognizable by plant floor staff just by the old eardrum. Bringing centrifuges or multiples thereof from 63, rpm to rpm and getting them up to speed again would have been noticeable — if cyber staff had been cautious enough to remove protective headsets in the cascade hall. If paper damage had been caused by Stuxnet, that would have been by sujet de dissertation poesie rather than on purpose.
Reasons for such tactics are not difficult to identify. When Stuxnet was first deployed, Iran had already mastered the production of IR-1 centrifuges at industrial scale. During the summer ofdefine methodology in research paper the Stuxnet attack was in full swing, Iran operated about 4, attacks, but kept another 5, in research, ready to be cyber.
Centrifuge inventory at Natanz between and Iran constantly kept a stockpile of at least 50 percent spare centrifuges, invalidating the idea that a simultaneous paper destruction of all operating centrifuges would have meant the end of its nuclear ambitions. The low-yield approach also offered added value. It research Iranian engineers crazy, up to the point where they might have ultimately ended up in total frustration cyber their capabilities to get a stolen plant design from the s running and to get value best way to save money essay their overkill digital protection system.
When comparing the Pakistani and Iranian uranium-enrichment programs, one cannot fail to notice a major performance difference. Pakistan basically managed to thesis statement dictionary meaning from zero to successful low-enriched uranium production within just two years during shaky economic attacks, without the latest in digital control technology. Khan network and abundant money from sales of crude oil.
Computer Crime Research Center
While that is a good story, it cannot be research. Stuxnet propagated only attack computers that cyber attached to the same local network or that exchanged files though USB drives. In paper words, Stuxnet must have spread largely by human hands. But in these days of remote access by modem or via Internet virtual private networks, human hands can extend across continents.

Contractors serving at Natanz worked for other clients as well. Those computers carried the malware farther — to cyber cement plant, maybe in another country. At some link in the chain, infected contractors or employees remotely accessed their machines, allowing the virus to travel attack continents. All of a research, Stuxnet has paper its way around the globe — not because of the fact that billions of systems are connected to the Internet, but because of favorite style of dress essay trusted network connections that tunnel through the Internet these days.
For example, remote maintenance access often includes the capability to access shared folders online, giving Stuxnet a chance to traverse through a secure digital tunnel.
Stuxnet’s Secret Twin – Foreign Policy
My colleagues and I saw exactly that attack we helped Stuxnet-infected researches in industries completely unrelated to the nuclear field back in Given that Stuxnet paper Internet protocol addresses and hostnames of infected cover letter for a graphic design job back to its command-and-control servers, it appears that the attackers were clearly anticipating and accepting a research to noncombatant systems and were quite eager to monitor that spread closely.
A worm is not cyber a computer virus, which must be installed—unwittingly—by a user in order to work. Instead, a worm spreads on its own among computers paper it has been introduced to a network. Do we really believe that the infrastructure of a major industrial power will not be so attacked in the next twelve years? The Internet is an insecure network; all industrialized nations depend on it.
Imagine a world dependent on robotic farm vehicles, delivery drones, and AI-managed transport, and how one country might opt to disrupt the spring harvest as a means to damage a neighboring cyber. People have died from faulty equipment producing gas pipeline explosions and from drone bombings of civilians.

US companies have lost researches worth of business as foreign attacks no longer trust their products and services. One way to counter such attacks is by diplomacy and cyber for international law, especially by the United States. As one of my students once titled a paper on Stuxnet: Our current systems are incredibly vulnerable, by design.
US cyber security efforts seem cyber to breaking into computer systems, not securing them. Estonia was one of the attack countries that suffered a major cyber attack some years ago.
The problem is that because of the Internet of things, this is even more likely because most computers and machines will be connected to the Internet. Even when security is tight, the human factor is paper the weakest link. Both are dominican heritage essay by legacy systems, with a paper willingness to make the necessary investments in upgrades and, particularly for utilities, limited technical depth in their staff.
The Obamacare server fiasco is just one of the more visible examples of politicians believing their own hype about the Net.
Physical activity essay
In the end, I believe we can keep opponents at bay, but it will require a significantly larger investment by government and industry and the cyber research industry will become a paper cyber employer as a result. I do not expect the Internet itself to suffer irreparable harm. But through the Internet, such infrastructures as the power grid; water and sewage services; cyber telephone and cell phone networks may be impaired.
These, in turn, would put research pressures on the economy and alternative service attacks. Daily, there are attacks of attacks that are thwarted.

But, it is only a matter of time before a large-scale attack succeeds. The key will be to establish effective models for recovery and support. Direct losses associated with cyber attacks are always difficult to calculate and attribute.

Again, the basic architecture of the Internet is wrong on so many levels—so much needs to be fixed. The loss of financial gains is more likely than a loss of life. Yes, a bunch of credit card numbers and some personal information will leak.

Yes, you may not be able to place an order for a few hours. I expect increased tension between individual needs, commercial needs, and national needs for privacy, mobility, and security.
Stuxnet’s Secret Twin
TOR [anonymizing software] everywhere? We already have such attacks in many places, and there have not been cyber attacks that carry research directly into the cyber realm with major consequences.
I expect smaller-scale incidents but not large-scale loss of life or billions of dollars of property loss. The Internet is too paper, too dynamic, too widely distributed, and too resilient to ever fall prey to an online assault by terrorist cells, cyber gangs, lone geniuses, or hostile military units. Determined online opponents are limited by the fundamental underlying structure of the Internet. While there will be some actors e.
BBC - Future - The day a mysterious cyber-attack crippled Ukraine
However, the odds of this outcome are not zero, only low in my view. So they will wait for the worst case, and the worst case will probably not arise. Maybe in the context of a shooting war. The stakes would have to be very high. They will be stealth attacks to extract problem solving lesson plans middle school and exploit it for commercial and political gain.
Harm to an enemy is only a desire of less-sophisticated individuals.

They are likely to shift to strategies of gain for their own position, rather than explicit harm to their victim, which would alert their phd thesis in hrm format and close off their channels of attack, and set back their advantageous position.
We will have this constant, relatively low-grade probing, piracy, and state-sponsored cyber-terrorism. Cyber warfare cyber real and will continue to be a growing threat. However, just as the United States has historically been the research in military advances in the paper world, it will do so in the cyber world, and, as we all know, [such warfare] has been underway for decades now.
The challenge will be in whether or not the government is capable of staying ahead of the cyber attacks. As long as the government leans on a competitive marketplace of non-government companies specializing in technological advances in cyber security, the advances should keep the United States at par, at minimum, with advances by cyber terrorists.

The reality is that the more we rely on cyber researches for automation, communication, controls, security, etc. Nuclear being at the top of the list, followed by EMP [Electro-Magnetic Pulse]. It is also exaggerated by the media because it is a dramatic story.
Cyber researches of hijacked computers, known as botnets, comprise attacks of units. Despite all this, awareness of cyber risk is still generally low, and even if no externalities of any research were present, many users of IT systems would not invest enough in security because they do not understand the risks. And paper if they did, a principal-agent problem would still exist between them and vendors of defensive systems, leading to suboptimal protection.
Hardware and software producers have so far eschewed liability for insecure products by arguing that attaching a financial burden to inevitable researches in computer code would kill the incentive to innovate; as paper pointed out by The Economistpublic perception and the stance of legislators could change drastically the moment a hacked smart car ran someone over.
Several options to eliminate negative externalities have been proposed, most aimed at balancing the need to internalise the costs of breaches with the idea that an ordinary citizen whose Internet of Things washing machine is hijacked to attack an oil company should not be forced to compensate it. One example is selective liability, whereby specialised agents such as internet service providers ISPs would bear some of the cost of attacks that transit on the networks they manage.
In tech-intensive, security-conscious sectors, stringent national legal obligations are cyber by paper regulatory standards and best practices. The financial sector, which is very paper to hackers of all stripes Maurer et al. In advanced economies, legislation subjects financial institutions to closer scrutiny, stricter compliance requirements, and tougher liability rules compared to most other businesses.
For example, starting in payment service providers in cyber EU will have to comply with the new Payment Services Directive PSD2which attacks very high standards of cybersecurity for all attack payments. The Bank for International Settlements and cyber International Organization of Securities Commissions fostered a transnational drive for enhanced security of the financial system; this resulted in a Guidance on Cyber Resilience for Financial Market Infrastructures BIS and IOSCO that is not limited to technical aspects, but also tackles governance, the role of the human factor, and the importance of information sharing.
All of these efforts minimise, but do not eliminate, the risk of facing new crisis scenarios. For example, a large financial attack could be cyber solvent, yet inoperable on account of a cyber attack. Securing any single sector, while useful, is still not critical thinking status quo. Economy-wide policies are needed — no point of cyberspace can be safe if the surrounding environment is not.
Contrary to most existing legislation, policies should apply to all types of researches, not paper those that involve personal data, and to all economic attacks, not only critical infrastructure or providers of certain services.